What is a VPN?
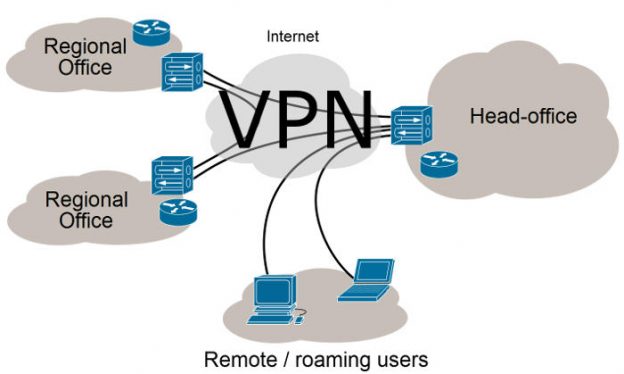
A VPN, which stands for virtual private network, is an encrypted network between one or many machines (clients) and a server. It is “virtual” in the sense that it is not a direct physical or WiFi based network. The machines securely connect over an internet connection and define an entirely new set of internal IP addresses by which they communicate. This provides a private network which cannot be snooped on, even by the client’s internet service provider (ISP). It is one of the best network security mechanisms available.
Various communication protocols can be changed by network software to route requests for the services over the VPN instead of the client’s main internet connection. Typically the HTTP and HTTPS web browsing requests are re-routed to the VPN connection, but it is also common for things like Windows file sharing or BitTorrent to also be re-routed. Services like printers are often not re-routed through the VPN because one would typically print a document to a printer local to their location.
Why Should I Use One?
There are several common scenarios for using a VPN. The technology really took off to enable work related data sharing amongst geographically diverse offices of a company.
On the Job
The most common use of VPNs is in a business environment. It is a common corporate need for employees regardless of their location to be able to access shared but company internal documents, tools, and websites. These can include file shares, Sharepoint sites, time tracking software, version control software, databases, etc.
The company often provides its employees a computer with the VPN client already installed. The client connects to the corporate VPN servers with a username & password combination, or sometimes a private certificate key. Once connected, the employee can utilize the internal tools via share names and sites that would not work without the VPN connection.
Personal: On the Road
 With the proliferation of public WiFi hotspots, any WiFi enabled device is easily connected to the internet. Coffee shops, airports, restaurants, gyms, hotels, and other public places make connecting quick & easy. There are several important points to keep in mind when using unsecured public internet connections:
With the proliferation of public WiFi hotspots, any WiFi enabled device is easily connected to the internet. Coffee shops, airports, restaurants, gyms, hotels, and other public places make connecting quick & easy. There are several important points to keep in mind when using unsecured public internet connections:
- Your MAC address is visible to the provider. Every device that communicates on the internet has a unique fingerprint called a MAC address. This is visible to the provider – even if you do not connect to the network. A coffee shop owner can determine, for example, that your device comes into his shop every day around 7am. He can correlate that you physically come in at that same time, and that the device with MAC address 07-94-C7-3A-F1-8D most likely belongs to you.
- Your traffic is visible to the provider. His router logs will allow him to determine that a given device on his network visited various websites. This is true even if you use SSL via HTTPS. With HTTPS the content will be encrypted, but he could still determine that you probably have a bank account with Wells Fargo since you went to their site. Any requests made using HTTP are not encrypted, and the full content of your browsing could be snooped.
- Your traffic may be visible to others on the network. If the network is truly public, in that no password is required to connect, then the connection is likely not encrypted, and it is possible that in addition to the provider, other users on the network could also snoop on your web traffic.
If you connect to a VPN when using a public hotspot, then all of your traffic will be encrypted and routed securely to the VPN server. The VPN server will then route your request to the original intended destination, such as a website. To that destination, the request will look as if it came from the VPN server, not from your device.
The provider would still see that the device likely belonging to you made the initial connection to the VPN, but after that, he will not be able to discern any requested sites or contents of those requests. He will only be able to determine the number of bytes sent between you and the VPN server.
Personal: At Home
The situation with your at home internet connection is not much different from the public scenario discussed above. The provider in this case is your ISP. Of course if you are using your own WiFi, you should have enabled password protected encryption so no one without the password can connect to your home network. This mostly eliminates the risk of 3rd party snooping.
The same issues apply with your ISP however. They can still see everywhere you travel on the internet if you take no preventative action. Connecting through a VPN will similarly allow them only to see that you are connecting to the VPN server. After that, they will be completely unable to track where your requests go, or the content of those requests.
Free vs. Pay VPNs
With privacy becoming more and more of a concern, the number of organizations offering VPN services has grown. There are free and premium VPN services. Typically the free services will serve ads, not be as fast, and not offer as many servers to connect with.
The premium services will usually not serve ads, have faster performance, and offer many VPN servers around the world to which you may connect. They will often be easier to get up and running, and will have clients for a wider set of devices: Windows, Mac, Linux, iOS, Android.
If you are truly looking to maximize privacy, one key attribute to consider is location of the VPN server and whether the organization operating the server keeps logs. Privacy protection laws will often vary depending upon the jurisdiction where the server is kept.
 In our experience, NordVPN provides a tremendous overall experience, with wide ranging device support, ease of use, and fast performance. Full disclosure: we enjoy the service so much that we are a member of their affiliate program. If you join the service from here, you will pay no more, but we will receive a small commission that helps keep PrepperSoft running.
In our experience, NordVPN provides a tremendous overall experience, with wide ranging device support, ease of use, and fast performance. Full disclosure: we enjoy the service so much that we are a member of their affiliate program. If you join the service from here, you will pay no more, but we will receive a small commission that helps keep PrepperSoft running.
Regardless of which service you choose, we hope that the case is clear that if you value your internet privacy at all, you should be using a VPN service.



Thank you for an easy to understand definition of VPNs and why we need them.